For Administrators, Developers and Office Workers
Prerequisites:
- Computer running Windows 10 Enterprise/Education, version 20H1 / 20H2 (most of
these settings will apply to older versions of Windows 10 or lower SKUs, but
compatibility is not guaranteed). - TPM module.
User roles
Not all policies are suitable for all types of users. For this reason, we will be analyzing the
suitability of each policy for two types of users depending on their role:
Administrator/Developer – Uses an administrator account, launches a lot of software,
and connects different accessories and hardware.
Office Worker – Uses a standard account and the set of their software is limited. Office
Workers do not change hardware and accessories without the assistance of the IT
department.
1. EFI (BIOS) Configuration
- Many of the modern Windows 10 features rely on hardware and firmware support, therefore it is necessary to properly configure the system’s EFI.
- Due to major differences between EFI configuration interfaces of various manufacturers, we cannot provide exact steps. Some of the below mentioned options will feature a different name or will be missing entirely on some systems.
To be enabled:
- Secure boot
- Intel Boot Guard
- Intel VT-x \ Intel VT-D \ AMD-V \ IOMMU \ virtualization support
- Execute Disable Bit
- BIOS administrator password
- TPM module (on systems with both hardware and firmware option is hardware
preferred) - Device Guard
- DMA Protection
To be disabled:
- Compatibility Support Mode (CSM) support
2. Windows Defender Firewall
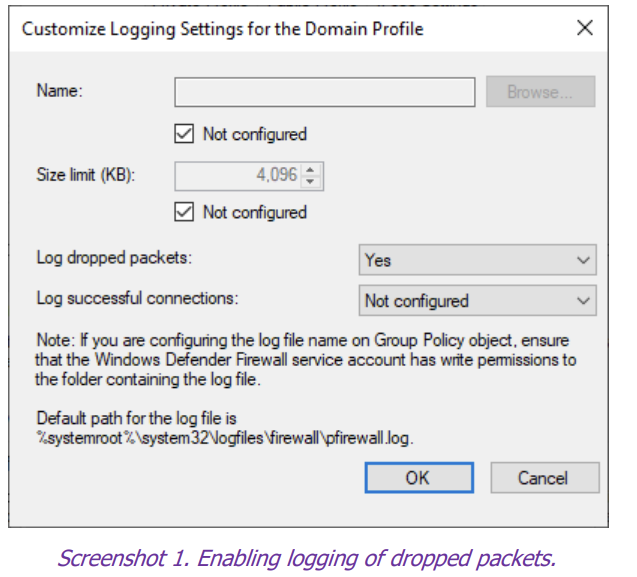
Enable logging of dropped packets
Policy path: Computer Configuration\Windows Settings\Security Settings\Windows
Defender Firewall with Advanced Security\Windows Defender Firewall with Advanced
Security.
Right-click on Windows Defender Firewall with Advanced Security and select Properties.
Under Logging, select Customize and enable Log dropped packets